CYBERSECURITY & LAW
Security verification, including pen testing
Buy peace of mind with Knowit's cybersecurity services.
In our fast-paced, ever-changing world, high demands are placed on continuous control of companies' cyber security. Security requirements have several sources, apart from your own organization they may come from customers, partners, legal authorities, and standards among others.
It is often an advantage to bring in an independent third party who can make objective analyses that take all aspects into account. Our experienced Cybersecurity experts help you control the organization's IT systems and critical business functions. After our extensive review, you will have a good overview of what risks exist and receive suggestions on how to prevent or remediate them. Our Technical Security Reviews are based on each organization's special conditions and needs.
Different forms of penetration testing
Penetration tests can look quite different depending on the system being tested. We at Knowit have extensive experience with penetration tests and carry out tests against, among others:
- IoT
- Mobile applications
- Web applications
- API
- Network and infrastructure
- Public and private clouds
Find technical vulnerabilities and identify business risks
Regardless of the scope of the penetration test, the result provides good insight into the security risks of the tested systems.
Knowit works according to a proprietary methodology for penetration tests that is based on PTES (Penetration Testing Execution Standard). By following this methodology, we can be clear in our scope, our execution, and the expected result.
In our reporting, we highlight both technical vulnerabilities and business risks, and we also try to identify root causes and produce recommendations for how security work at an organizational level can be improved.
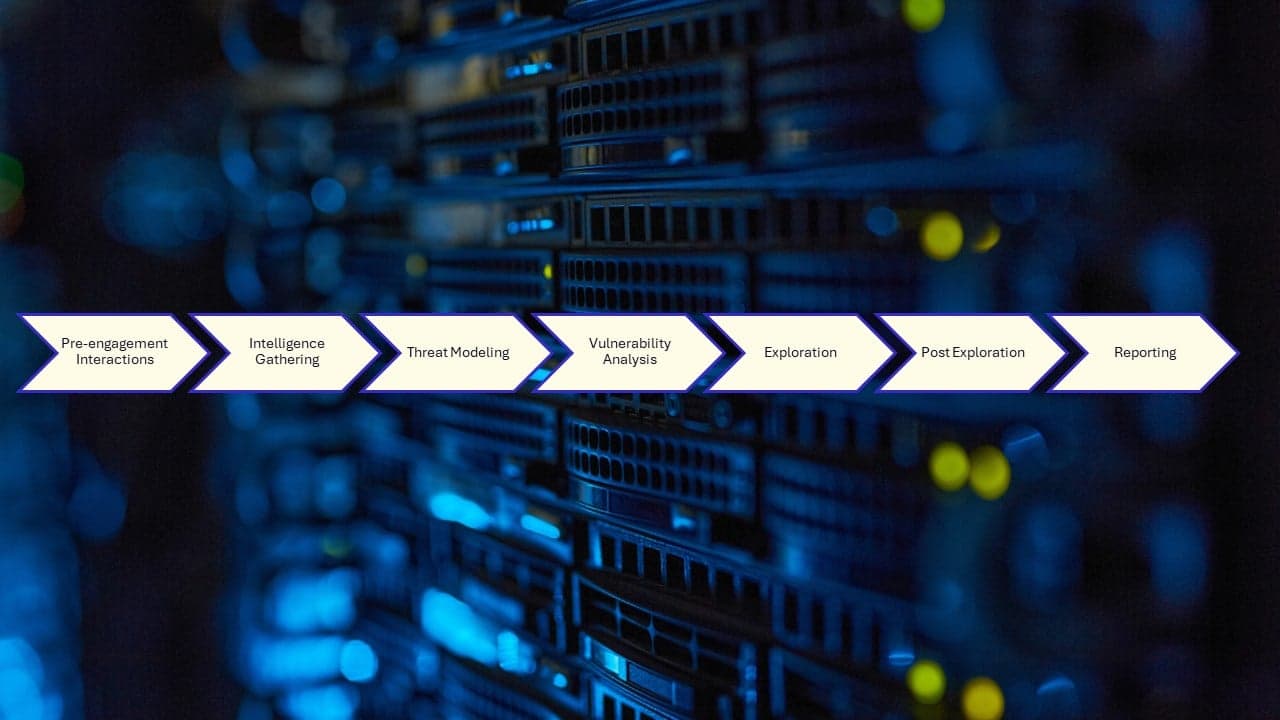
PTES (Penetration Testing Execution Standard).
Contact us
Do you want to know more? Welcome to contact us for further information.

Pernilla Sander
Sales